Am I Cyber Resilient ?

Resilience – Definition
The Oxford English Dictionary defines "resilience" as "the capacity to recover quickly from difficulties; toughness" and also "the ability of a substance to return to its original shape after being bent, stretched, or pressed"
So what does it mean to be Cyber Resilient?
The focus of the word ‘Resilience’ is on the ability to recover quickly when bad things happen. In the world of Cyber Security this could mean a Data Breach of Sensitive information, Ransomware locking you out of your core systems or a Cyber disruption to a Key Supplier that has a knock-on impact on your operations. Essentially it means are you able to recover FAST (and within your defined Business Impact Tolerance) when ANY TYPE of Cyber related event occurs?
This is really where the rubber hits the road – the Cyber teams nightmare scenario and one they should be prepared for. We have seen many examples in recent months where large organisations have kindly showcased to all Boards, Security and Risk Leaders and Regulators what the real world business impacts look like – think M&S, LandRover Jaguar, Co-Op.
Being Resilient Means Being Prepared
Cybersecurity resilience means an organisation's ability to anticipate, withstand, recover from, and adapt to adverse cyber events such as attacks, disruptions, or system failures. The emphasis is not only preventing and defending against threats, but also ensuring that essential business operations can continue and recover quickly even when security is breached or systems are compromised.
Key Principles
- Cybersecurity resilience requires strategies for anticipating threats, withstanding attacks, recovering systems and data, and adapting processes based on lessons learned from incidents.
- It is broader than traditional cybersecurity, as it assumes breaches are inevitable and focuses on maintaining business continuity under adverse conditions.
- Components include preparation (risk assessment, disaster recovery planning, immutable backups), detection (monitoring, alerts), response (incident handling), recovery (restoring operations), and adaptation (the feedback loop / improving defences based on experience).
Why It Matters?
Cybersecurity resilience allows organisations to limit damage from cyber incidents, minimise downtime, and retain trust among customers and regulators, all while ensuring critical functions remain operational even during an ongoing attack or disruption.
Is Cyber Resilience Different across Business Sectors?
Yes – there are significant differences across sectors in how cyber resilience is understood, implemented, and prioritised largely driven by each sector’s regulatory requirements, business objectives, risk tolerance, and operational dependencies.
Key Sectoral Differences
- In critical infrastructure sectors like government, utilities, and finance, the main driver for cyber resilience is continuity of operations and national security. These have very low risk tolerance and prioritise maintaining essential services during and after an incident. There is also a heavy Regulatory stick globally (EU Digital Operational Resilience Act - DORA, UK Cyber Security and Resilience Bill (CSRB)) pushing organisations that meet critical infrastructure thresholds to have formal structures in place including regular testing regimes. Critical third parties now including the main Cloud Platform providers will also fit into this bucket,
- In private industry, economic considerations often play a larger role. Businesses may balance operational continuity, cost-effectiveness, and protecting intellectual property depending on what is most valuable to their enterprise and the risk/reward decisions they make.
- The public sector may move more slowly in adapting to new threats due to long-term planning, complex and aging technologies and regulatory constraints, whereas private sector organisations can sometimes respond and adopt cyber resilience innovations more rapidly.
- Across sectors, there remain gaps in universal standards and metrics for measuring success in cyber resilience, meaning that organisations in different industries may take divergent approaches to achieving and demonstrating resilience.
Building a Cyber Resilience Framework – where do I start?
Essential to becoming Cyber Resilient is putting in place a Cyber Resilience Framework, In essence these are the policies, principle, guidelines and best practices your organisation will put in place to build your ability to withstand, recover from and adapt to evolving cyber threats including external attacks. This should sit under the umbrella of the business’s cause agnostic Crisis Management and Business Continuity plans for overall Operational Resilience.
The NIST Cybersecurity Framework (CSF) provides an internationally recognised structured model and is a good place to start.
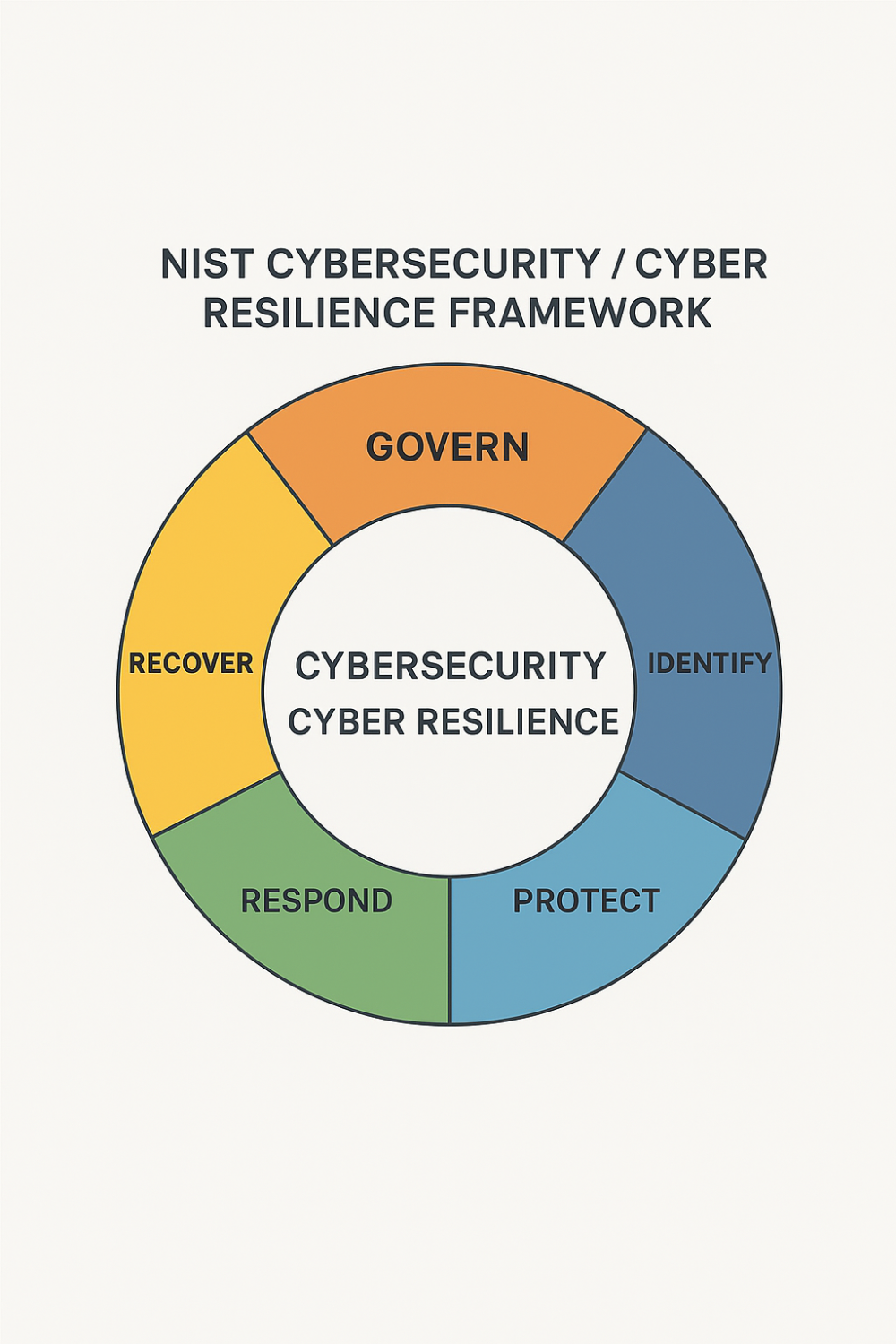
The broad scope across the 6 domains cover:
- Identify risks and critical assets – have a comprehensive view of the assets under Cybersecurity protection, the user base across those assets and maintain and up to date view of risks and the overall threat landscape of your business operation.
- Prevent and mitigate threats – implementation of robust security controls eg. Data encryption, multi-factor authentication, network segmentation
- Detect cyber events and anomalies – deploy continuous monitoring and behavioural analytics using SIEM, IDS/IPS and other tools to detect unusual activity quickly plus regular assessments and integrity checks to identify anomalies and potential breaches.
- Respond to incidents – put in place a clear, repeatable and tested response plan for containing and mitigating incidents
- Recover business operations – ensure high availability in line with business risk appetite through business continuity planning, redundant systems and multi-location data replication AND apply strategies for rapid failover, resynchronisation and full service restoration to minimise downtime
- Governance and continuous improvement – perform post-incident reviews to learn and evolve defences and update frameworks, plans and cybersecurity investments based on evolving threats, lessons learned and evolving business needs. Risk management and governance structures should be integrated to oversee Cyber Resilience implementation and ongoing evolution.
Other framework examples include ISO27001 and related standards, UK National Cyber Security Centre’s Cybersecurity Assessment Framework (CAF) and MITRE’s cyber resiliency design principles. Pick the one(s) that best meet your business needs.
How can I measure Cyber Resilience?
Cyber resilience can be measured using a variety of metrics that focus on an organisation's ability to detect, respond to, contain, recover from, and adapt after cyber incidents. Key metrics commonly used include:
- Mean Time to Detect (MTTD): The average time between the start of a cyberattack and its detection by the organisation, indicating detection capabilities.
- Mean Time to Acknowledge (MTTA): Time from an alert being triggered to the initiation of a defensive response.
- Mean Time to Contain (MTTC): The time it takes to contain a threat and prevent further damage after detection.
- Mean Time to Resolve (MTTR): The total time required to fully resolve the incident and restore operations.
- Recovery Time Objective (RTO) and Recovery Point Objective (RPO): Targets for how quickly critical systems should be restored and how much data loss is acceptable after an incident.
- Security Policy Compliance Rate: The extent to which employees and systems comply with security policies, often measured via audits or automated checks.
- Employee Awareness and Phishing Click-Rate: Metrics to gauge human cyber resilience, such as employee knowledge and susceptibility to phishing attacks.
- External Security Ratings: Third-party security ratings provide an outside-in view of an organisation's cybersecurity posture.
More comprehensive frameworks consolidate many such indicators into categories reflecting the organisation’s ability to avert social engineering, address vulnerabilities, resist malware and intrusions, handle incidents, protect assets, and minimise damage, often aligned with models like the Cyber Kill Chain.
These measures enable organisations to quantify their cyber resilience, identify areas for improvement, and communicate resilience levels meaningfully to stakeholders and leadership.
In practice, tailoring metrics to organisational priorities and regularly tracking them over time helps maintain and improve cyber resilience effectively.
Is Cyber Insurance part of being Cyber Resilient?
Cyber insurance is an important component of an overall cyber resilience strategy, but it is not synonymous with being cyber resilient. Rather, cyber insurance serves as a financial safeguard that helps a business recover and maintain continuity when a cyber incident occurs, complementing the technical and procedural measures that make up a resilience framework.
There is a close correlation between the maturity and effectiveness of an organisations Cyber Resilience Framework and the level and coverage of Cyber Insurance it can negotiate. But like all insurance it will come with exclusions and caveats and should only be considered as a backstop if all else fails not protection in and of itself.
In Conclusion – how do I know if I am Cyber Resilient?
Bottom line is you are only going to know how Cyber Resilient you really are if you have to deal with a real world Cybersecurity incident no matter how many dashboard metrics you may have. However, the next best thing is to TEST, TEST, TEST. The time to find out if your supposedly immutable backups really are just that is not in the heat of battle when you are struggling to rebuild your services after a Ransomware attack! As the old adage goes ‘Fail to Prepare, Prepare to Fail’.
The NuroShift View
Today’s Cybersecurity Leaders face challenges across all fronts when it comes to providing the requisite assurance to their organisation leadership, third parties and external regulators. In a world where doing more with less is becoming the norm, getting to a place where you have confidence you have done enough to be prepared for not if, but when, the cyber event happens requires a structured and integrated approach that can be measured with clear and robust metrics.
At NuroShift, we combine strategic thinking and deep technical expertise with structured methodologies to help clients:
- Identify gaps and areas for improvement in existing structures - people, process and technology led controls
- Design and Implement a Cyber Resilience Framework fit for their individual business needs using established frameworks
- Measure their Cyber Resilience over time accounting for changes to internals controls and the Threat Landscape.
- Meet Third Party and Regulatory Requirements and Expectations
For more thought leadership articles like this, take a look at our Insights page:https://www.nuroshift.ai/blog
Clare brings over 25 years of experience in technology and cybersecurity, including leadership roles at Visa Europe as Head of Risk and Compliance for the global cybersecurity organisation. She led successful Bank of England CBEST exercises, oversaw global PCI programs, and supported post-acquisition due diligence and integration across multiple M&A initiatives. Prior to Visa, she spent two decades in consulting with DMW Group and Accenture, delivering global, large-scale IT transformation initiatives. A Durham University graduate, Clare is a passionate runner and dog walker outside of work.


.jpg)
